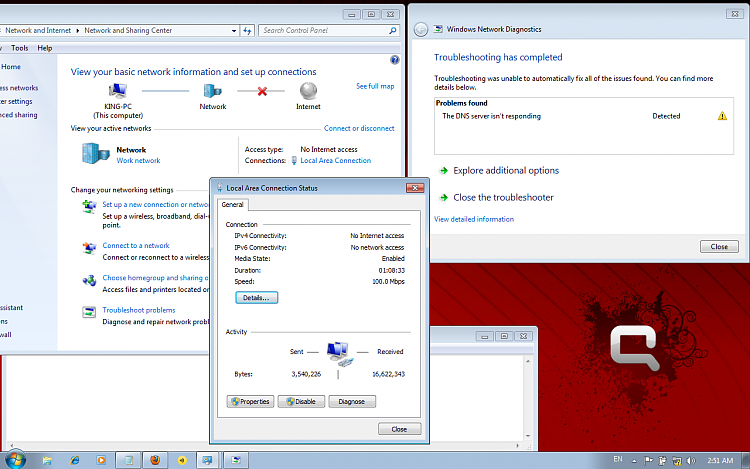
The Domain Name System (DNS) underpins the web we use every day. It works transparently in the background, converting human-readable website names into computer-readable numerical IP addresses. DNS does this by looking up that information on a system of linked DNS servers across the Internet. Computer Configuration Follow New articles New articles and comments. Get instructions for Windows, Mac, mobile phones, and more. Using DNS over HTTPS (DoH) with.

We’ve learned how to protect ourselves from a DNS leak, and today we’re going to explore a new and recurrent threat to your network. We’ll take a deeper look into what DNS hijacking is, what makes DNS so susceptible to these types of attacks and how you can discover DNS hijacking before it causes any damage.
What is DNS hijacking?
DNS requests are mostly unencrypted, and this creates a problem as well as room for intercepting requests by malicious attackers. We’ve touched upon DNS and issues with its privacy, but let’s get into how and why DNS hijacking is performed.
DNS hijacking, also known as DNS redirection, is a method of DNS attack in which attackers attempt to incorrectly resolve your DNS queries and redirect your traffic to a malicious website.
While your browser is resolving a URL, a fake server set up by the attackers will send a fake IP address that belongs to their malicious website to your device—in hopes of tricking you into using the unauthorized version of the website you want to access. These are often websites where users input their sensitive data, allowing attackers to steal their data.
There are a couple of ways in which DNS hijacking is used. One of them is for pharming. Pharming is a type of attack that redirects website traffic to a malicious one. This is done by manipulating the user’s computer, changing the host file or exploiting the DNS server. One example of pharming is when you’re on the internet and a website you want to access redirects you to a malicious one filled with unwanted pop-ups and ads. The primary motive behind pharming is generating revenue.
DNS hijacking can also be used for phishing. In phishing, victims are targeted and attackers attempt to trick them into revealing sensitive information, like their payment credentials. The most common scenario we see in phishing is sending an email as bait, directing users to a website that appears to be a legitimate payment processing website, and from there, steal their information. If you suspect that a domain is being used for phishing, be aware that you can easily detect phishing domains by using passive DNS.
ISPs also perform a type of DNS hijacking. While this is not as dangerous as attackers performing DNS hijacking, it’s still something that can make people feel less secure and puts their privacy at risk. ISPs take over your DNS queries, collecting data so they can, in turn, serve you ads while you try to access a non-existing domain. Normally if you typed in a nonexistent domain, you would get a response telling you as much, but as your ISP is DNS hijacking you, you instead get redirected to a website full of ads. Which is not dangerous per-se, but if those websites and ads are malicious you could be presented with a security risk.
One of the most famous DNS hijacking campaigns took place in late 2018, when a huge DNS hijacking campaign dubbed DNSpionage was uncovered and reported by Cisco Talos. The attackers were stealing credentials from government and private sector employees in the Middle East and North Africa by hijacking their DNS servers.
Krebs on Security did extensive research on the case, going so far as to share how SecurityTrails Passive DNS API was used to pinpoint changes to DNS records of domains that were tied to the campaign. We suggest checking out the full article to see all the interesting things Brian uncovered.
Stay in the loop with the best infosec news, tips and tools
Follow us on Twitter to receive updates!
Types of DNS hijacking
DNS hijacking attacks are grouped in these four types:
| Local DNS Hijack | In this type of DNS hijack, attackers install Trojan malware into your computer and change your local DNS settings to redirect your traffic to malicious websites. |
| Router DNS Hijack | This attack considers hacking into DNS routers, changing the settings and affecting all users connected to that router. |
| Rouge DNS Hijack | After a DNS server is hacked, the DNS records can be changed to direct all traffic by the user to a malicious website. |
| Man in the middle DNS Hijack | Here, the attacker intervenes in the communication between the user and the DNS server, and serves a fake IP address that will redirect the user to a malicious website. |
Detect DNS hijacking
Common signs that you’ve been DNS hijacked include web pages that load slowly, frequent pop-up ads on websites where there’s normally none, and pop-ups that tell you your computer has been infected with malware.
While these can be common indicators of an attack, we can’t identify DNS hijacking with certainty based solely on them. Thankfully, there are several online tools you can use to determine if you’ve been attacked, or you can use your OS’s terminal to diagnose it:
Using the ping command
The easiest and most effective way to discover DNS hijacking is by pinging a non-existing domain using the ping utility directly from your terminal.
If the results confirm that the IP doesn’t exist, you’ll know you haven’t been DNS hijacked. In contrast, if the result is resolved there’s a big chance that you’re a victim of DNS hijacking.
Router Checker
Malware can infect your router, giving attackers access to the router administration page and allowing them to change its DNS settings to use malicious servers. When this happens, you’ll be automatically redirected to the attackers’ websites.
To check if your router has been infected, your first step is to check its DNS settings, but there’s a great online tool that can do this for you.
Router Checker from F-Secure labs is a tool that verifies if your router is connected to its DNS resolver, and that it’s using a legitimate and authorized DNS server. It’s really easy to use:
When you go to the website, simply click on the Router Checker button which will lead you to a new page, and from there just go to “Check your router.” In a few seconds, you’ll be presented with a response informing you whether you have any issues on your router and if it may have been hijacked by attackers.
WhoIsMyDNS.com
WhoIsMyDNS is another great online tool that helps you expose the actual server making DNS requests from your device on your behalf. If you don’t recognize the DNS that it displays, then you might have actually suffered a DNS hijacking attack.
How to protect yourself against DNS hijacking
There are a few basic steps we can all take to better protect ourselves from DNS hijacking or any type of DNS attack:
- Avoid clicking on any websites or links that appear suspicious, whether in your emails or on social media
- Inspect the URL and make sure that it belongs to a legitimate website
- Avoid the use of public Wi-Fi networks; they are almost always unencrypted so anyone can see your DNS traffic if they want to.
We’ve explored some ways you can protect yourself from domain hijacking, and many of them apply to DNS hijacking as well. Those tips didn’t require any special technical skill to implement, and today we’ll expand that list with a few more things you can do to keep you safe on the Internet, and to avoid DNS hijacking.
Deploying DNSSEC
Deploying DNSSEC, or Domain Name System Security Extension, is a critical step in protecting yourself against DNS hijacking. It’s one of the best technologies available that will ensure you a high level of DNS security.
Dns Server Software For Windows
DNSSEC fixes the problem of unencrypted data for DNS records by authenticating the origin of that data. This helps the DNS resolver know that the data it’s receiving is from a legitimate origin and has not been tampered with by malicious actors.
Unfortunately, deploying DNSSEC is not as simple as we wish it was. Many registrars just don’t have the necessary technology enabled in their domain name infrastructure and on the DNS server, and if they do, not all of them support all TLDs, so you may have limited options when looking for a registrar that enables DNSSEC.
We always suggest going to Cloudflare as they have an easy activation process for enabling DNSSEC. For more information, check out our full article on how to deploy DNSSEC.
Choose a more secure DNS server
Changing up your DNS server is a good way to protect yourself against DNS hijacking. By default your DNS queries will connect to your ISPs DNS servers. The services provided by your ISP don’t really keep someone safe while browsing the Internet.
Thankfully, there are plenty of choices to choose from. CloudflareDNS and OpenDNS are some of the more famous ones, but there are other great ones too. Some offer a higher level of online safety than others and many are free.
If you can’t decide on a DNS service provider, you can always check out our list of top 5 best DNS servers to improve your safety as well as your browsing experience.
Make sure your router is safe
Download Dns For Pc
Protecting your router is one of the most important steps in making sure you aren’t susceptible to DNS hijacking attacks. You can start by changing the default username and password since they are always the generic admin type;even an inexperienced attacker is able to guess it and gain access to your router. Also, keeping the router firmware up to date will ensure your safety from the latest vulnerabilities.
Use a VPN service
If you’ve ever heard anything about DNS security, VPN has always been associated with it. Using a VPN service, or Virtual Private Networks, is mostly associated with hiding your IP address so you can access content that is usually restricted (often by geo location) but its benefits extend much further than that.
When connecting to a VPN server, you are in fact creating an encrypted tunnel between your computer and the Internet, This allows information to be shared between two private parties, and protects it from stealing by malicious actors.
These steps to protect yourself from DNS hijacking are also important for your general online safety and we encourage everyone to try them out. There are of course more ways in which you can ensure you won’t be DNS hijacked, such as:
- Restricting access to your name server
- Restricting zone transfers
- Using strong anti-malware software
- Using script blockers in your browser
- Always patching unknown vulnerabilities on your server
- Placing legitimate DNS resolvers behind a firewall
Final thoughts
DNS hijacking is something that resurfaces every few years after nearly facing extinction. Attackers will always find new ways to compromise your data and gain access to your network and devices. What we can do is learn from publicized cases of DNS hijacking and not allow ourselves to be victims of malicious actors.
Practising good cyber hygiene is not only important to avoid DNS hijacking or other forms of DNS attacks, it’s a way to make the Internet safer and our online experience more comfortable. Following the tips we have shown you here, you can now not only detect if you’ve been a victim of DNS hijacking attack, you can also implement the proper security measures to avoid being one.
Try out our Passive DNS API to easily detect phishing domains and inspect DNS records just like Brian Krebs did in his research, or check out our passive intelligence tool SurfaceBrowser to discover all IP blocks, domains, subdomains, SSL certificates, open ports and much more about a target company!
Sara believes the human element is often at the core of all cybersecurity issues. It’s this perspective that brings a refreshing voice to the SecurityTrails team. Her ability to bridge cognitive/social motivators and how they impact the cybersecurity industry is always enlightening.
DNS Laptops & Desktops Driver Download For Windows
Get the best cybersec research, news, tools,
and interviews with industry leaders
