Premier/Diebold
Diebold made an uncounted number of apparently illegal changes in the election-conducting code between June and November. The memory cards on which the votes on each of the computers were recorded.
Make / Model: Premier AccuVote OS (aka ES 2000) & AccuVote OSX
Equipment Type: Hand-Fed Optical Scan Tabulator
The AccuVote OS is a hand-fed optical scanner and tabulator that processes hand marked paper ballots and ballots marked by the AutoMARK ballot marking device. The AccuVote OS is most often used as a polling place tabulator but in some smaller and medium-sized jurisdictions it is also used to tabulate absentee mail ballots.
The AccuVote OS scans ballots fed in any one of four orientations: face up, face down, head first, and foot first. It includes a small rectangular LCD screen displays ballot return messages for ballots that contain overvotes or undervotes. After scanning and tabulating ballots the AccuVote OS automatically drops counted ballots into one of two compartments into a ballot box, depending on ballot selection criteria specified by the election management software. The AccuVote OS can be configured to communicate with GEMS over a serial or modem connection.
- Customer Care Services & Support +1-800-343-2653 (24/7) CREATE A SERVICE REQUEST +49(0) 5251 2020 850 (Banking/General) +49(0) 5251 2020 855 (Retail).
- Diebold ATMs are getting hacked using a laptop & pirated Diebold ATM firmware Security at ATMs remains an issue affecting banking institutions around the world, experts from a hacking course mentioned. Recently, ATM manufacturer Diebold Nixdorf recognized an increase in jackpotting attacks against its ProCash model ATMs in some European countries.
In 1989 Unisys began marketing the ES-2000, originally developed by North American Professional Technologies, a subsidiary of Macrotrends International Ventures Inc. of Vancouver earlier in the 80s. Already by 1990 Unisys was selling the ES-2000 under the trade-name Accu-Vote. In late 1991, NAPT merged with Macrotrends to form Global Election Systems Inc. The corporation was technically Canadian, but the executive offices were in McKinney, Texas. Global immediately purchased a share in the patent rights of Data Information Management Systems. Through the decade of the 1990s, Global would grow to become a major force in the election equipment marketplace, largely on the strength of the AccuVote ES-2000.
In 2002, Diebold Inc., a well established manufacturer of bank vaults, automatic teller machines and other security-related products, bought Global to create Diebold Election Systems Inc. Global and Diebold continued to make the AccuVote ES-2000, although the name changed to the Accuvote OS, standing for Optical Scan, to distinguish it from the AccuVote TS, the touch-screen voting system that Global acquired with the purchase of I-Mark Systems.

In 2006, Diebold re-branded their election services department as Premier Election Solution and Premier purchased in 2009 by Election Systems and Software (ES&S) and was subsequently sold to Dominon Voting following a 2010 antitrust settlement.
After re-branding as Premier Election Solutions, the company announced its intentions of developing a hybrid optical scan/ballot marking device product to compete with the ES&S Model 100/AutoMARK combination that had proven successful in allowing jurisdictions to meet the accessibility requirements of the Help America Vote Act while retaining a paper ballot voting system.
In the end the AccuVote OSX was introduced in 2007 as part of the Assure voting system suite, which included the AutoMARK. The intake mechanism was modified for the OSX and a larger a sharper LCD screen for overvote/undervote protection.
The AccuVote OSX ballot box features three bins. The main compartment is divided into two bins, and there is a third bin in the door of the box. The AccuVote OSX uses the two internal compartments according to conditions set in GEMS and allows for the use of the bin in the door until the AccuVote OSX is replaced by a new unit, should a unit fail on Election Day. Access to the ballot box is protected by doors using locked compartments.
1. After you check in at the polling place, a poll worker will give you a paper ballot, which you will mark with the pen provided. Be sure to verify with the poll worker that you are using the correct pen for the machine used in your polling place.
2. Mark your choice on the ballot by darkening the oval (above right) next to your candidate’s name or selection. Follow the directions carefully to be sure your mark will count.
3. To cast a write-in vote, there are two steps: first, darken the oval for the Write-In position in that contest. Second, write the name of the person you are voting for on the line next to the Write-In oval. You must complete both steps to be sure your write-in vote will be counted!
4. When you have made all the choices you wish to make, review your ballot carefully. If you have made a mistake marking your ballot, ask a poll worker for another ballot.
5. When done voting, take the ballot to the scanning machine and insert it face up. If you have voted for more candidates for a race than can be elected (“over voted”), the machine may reject your ballot and will offer you the opportunity to correct your mistake. You may choose to submit your ballot as is, or correct the over-vote by marking a new ballot. (If you submit as is, your votes will be counted for all races except the over-voted race.) If the scanner is not working, your ballot will be secured to be scanned later.
Exceprt from HBO documentary Hacking Democracy (2006):
AccuVote OS usage in November 2020 (click for details)
Resources:
Integrity of Electronic Voting Systems: Fallacious Use of Cryptography, Computer Science and Engineering Department, University of Connecticut, 2011
Top to Bottom Review, California Secretary of State (2007)
Premier Source Code Report
Premier Red Team Report
Premier Documentation Report
Ohio EVEREST Review (2007)
Premier Executive Summary
Premier Technical Manager Report
Premier Technical Details Report
Final Academic Report
Systest Technical Report
Security Assessment of the Diebold Optical Scan Voting Terminal, UConn VoTeR Center and Department of Computer Science and Engineering,University of Connecticut (2006)
Security Seals
Ideally, the OS’s exposed ports, memory card access areas, ballot box doors and case seams would be covered with tamper-evident security seals. The integrity of these seals should be maintained at all times, and only breached under controlled, explained circumstances. Seals should be logged to maintain chain of custody of sensitive materials.
Keys
The keys for the AccuVote-OS are the same for all AccuVote-OS machines and are easily pickable with readily available tools. Care should be observed around the ballot box lock and the scanner key lock (turns the system off and on).
Ballot Box Access
Optical scan systems have at least one and possible more ballot boxes. Each ballot box should be inspected by a voter at the beginning of voting to make sure that they are empty. These ballot boxes should locked and/or be sealed with tamper-evident tape.
Memory Card Is Sensitive
Corrupt memory cards may be able introduce viruses, cause the main election server to crash and falsify votes. Access to the memory card should be controlled, monitored and logged at all times.
Correct Inks
Some Optical Scan systems have trouble reading red inks or inks with red in them. Voters should use the writing instrument provided at the polling place or, if voting at home, black ballpoint pen that does not bleed through paper.
Premier Voting Solutions
(formerly Diebold Election Systems)
1253 Allen Station Parkway, P.O. Box 1019
Allen, TX 75013
In 1979, Bob Urosevich founded American Information Systems and served as the President of AIS (now known as Election Systems & Software) from 1979 through 1992. In 1995, Bob Urosevich started I-Mark Systems, whose product was a touch screen voting system utilizing a smart card and biometric encryption authorization technology. Global Election Systems, Inc. (GES) acquired I-Mark in 1997, and on July 31, 2000 Mr. Urosevich was promoted from Vice President of Sales and Marketing and New Business Development to President and Chief Operating Officer. On January 22, 2002, Diebold announced the acquisition of GES, then a manufacturer and supplier of electronic voting terminals and solutions. The total purchase price, in stock and cash, was $24.7 million. Global Election Systems subsequently changed its name to Diebold Election Systems, Inc. In 2006, Diebold decided to remove its name from the front of the voting machines for strategic reasons. In August 2007 the company changed its name to “Premier Election Solutions”. Premier Election Solutions was acquired on September 2009 by Election Systems and Software (ES&S) and was subsequently partially acquired by Dominion Voting Systems on May 19 2010 following a 2010 antitrust settlement.
Diebold Nixdorf, which made $3.3 billion from ATM sales and service last year, is warning stores, banks, and other customers of a new hardware-based form of “jackpotting,” the industry term for attacks that thieves use to quickly empty ATMs.
The new variation uses a device that runs parts of the company’s proprietary software stack. Attackers then connect the device to the ATM internals and issue commands. Successful attacks can result in a stream of cash, sometimes dispensed as fast as 40 bills every 23 seconds. The devices are attached either by gaining access to a key that unlocks the ATM chassis or by drilling holes or otherwise breaking the physical locks to gain access to the machine internals.
In previous jackpotting attacks, the attached devices, known in the industry as black boxes, usually invoked programming interfaces contained in the ATM operating system to funnel commands that ultimately reached the hardware component that dispenses cash. More recently, Diebold Nixdorf has observed a spate of black box attacks that incorporated parts of the company’s proprietary software.

“Some of the successful attacks show a new adapted Modus Operandi on how the attack is performed,” Diebold Nixdorf warned in an active security alert that was issued last week and provided to Ars by a company representative. “Although the fraudster is still connecting an external device, at this stage of our investigations it appears that this device also contains parts of the software stack of the attacked ATM.”
The advisory said elsewhere:
In general, jackpotting refers to a category of attacks aiming to dispense cash from an ATM illegitimately. The black box variant of jackpotting does not utilize the software stack of the ATM to dispense money from the terminal. Instead, the fraudster connects his own device, the “black box,” to the dispenser and targets the communication to the cash-handling device directly.
In the recent incidents, attackers are focusing on outdoor systems and are destroying parts of the fascia in order to gain physical access to the head compartment. Next, the USB cable between the CMD-V4 dispenser and the special electronics, or the cable between special electronics and the ATM PC, was unplugged. This cable is connected to the black box of the attacker in order to send illegitimate dispense commands.
Some incidents indicate that the black box contains individual parts of the software stack of the attacked ATM. The investigation into how these parts were obtained by the fraudster is ongoing. One possibility could be via an offline attack against an unencrypted hard disc.
Mimicking the ATM computer
The growing number of attacks target the company’s ProCash line terminals, particularly the ProCash 2050xs USB model. The ongoing attacks are occurring in “certain European countries,” the advisory said.
AdvertisementBruno Oliveira, an expert in ATM security, said he had heard of the earlier form of black-box attack. The connected device manipulates the APIs included in OS extensions such as XFS or CFS, which communicate with remote servers operated by financial institutions. Black boxes, which mimic an ATM’s internal PC, can either be laptops or Raspberry or Arduino hardware that’s fairly easy to build, Oliveira said. Black boxes are one of four jackpotting techniques that Diebold Nixdorf describes here.
In some cases, the attached devices connect directly to the cash dispenser and issue commands for it to spit out cash. The other form of black-box attack plugs into network cables and records cardholder information as it’s relayed back and forth between the ATM and the transaction center that processes the session. The attached device then changes authorized maximum withdrawal amounts or masquerades as the host system to allow the ATM to dispense large sums of money.

The above-linked jackpotting brochure describes two other types of attacks. The first swaps out the legitimate hard drive with one created by the attackers. The other uses phishing attacks against bank employees. Once attackers obtain access inside the network of a financial institution, they issue commands that infect ATMs with malware that can be used to clean out the machines.
Good news and bad news
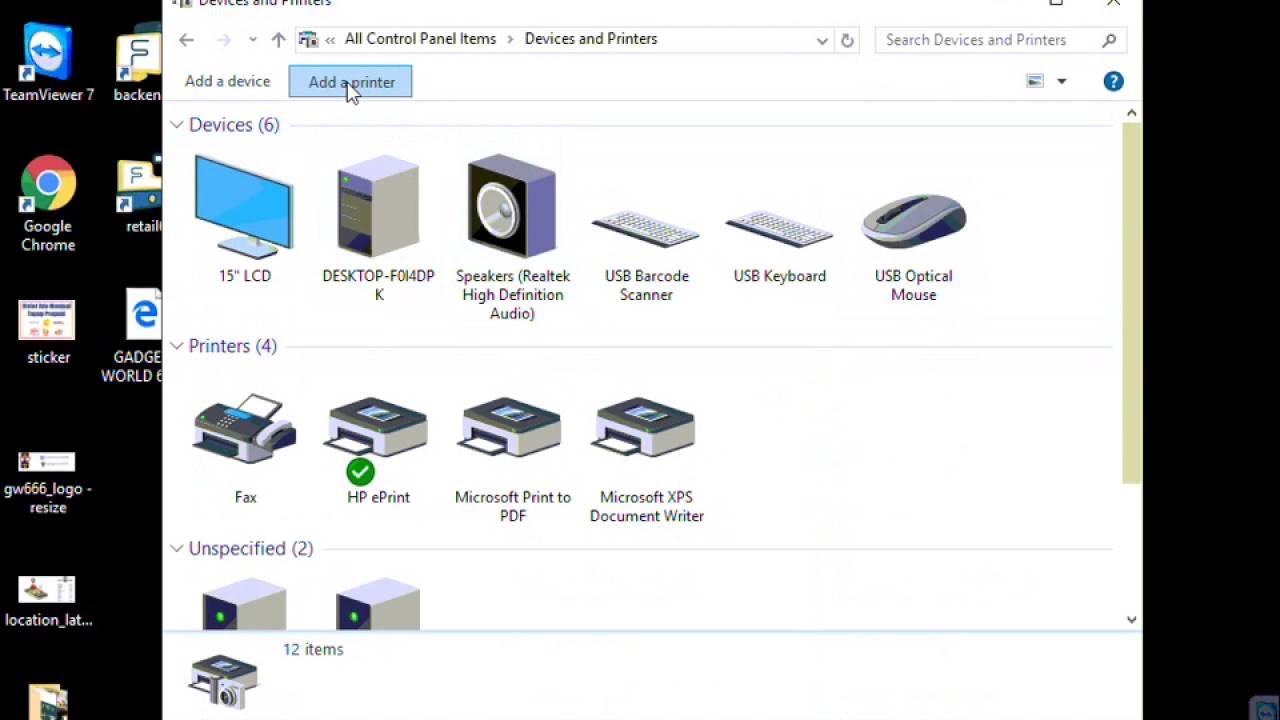
Diebold Laptops & Desktops Driver Download Windows 7
The new attack variation described by Diebold is both good and bad news for consumers. On the one hand, there’s no indication thieves are using their recently acquired software stack to steal card data. The bad news is that attackers appear to have their hands on proprietary software that makes attacks more effective. The recent increase in successful jackpotting ultimately results in higher fees, as financial institutions pass on the costs caused by the losses. Diebold has issued a variety of defenses that ATM owners can take to protect against the attacks.
Diebold Laptops Price
There’s little ATM users can do to prevent jackpotting. Still, it’s important to use only ATMs belonging to major banks and eschew those from mom-and-pop businesses. It’s also a good idea to shield the keyboard while entering PINs and to check bank statements each month in search of any unauthorized transactions.
